Page Not Found
Page not found. Your pixels are in another canvas.
A list of all the posts and pages found on the site. For you robots out there is an XML version available for digesting as well.
Page not found. Your pixels are in another canvas.
About me
This is a page not in th emain menu
Published:
A simple demonstration of the concept. 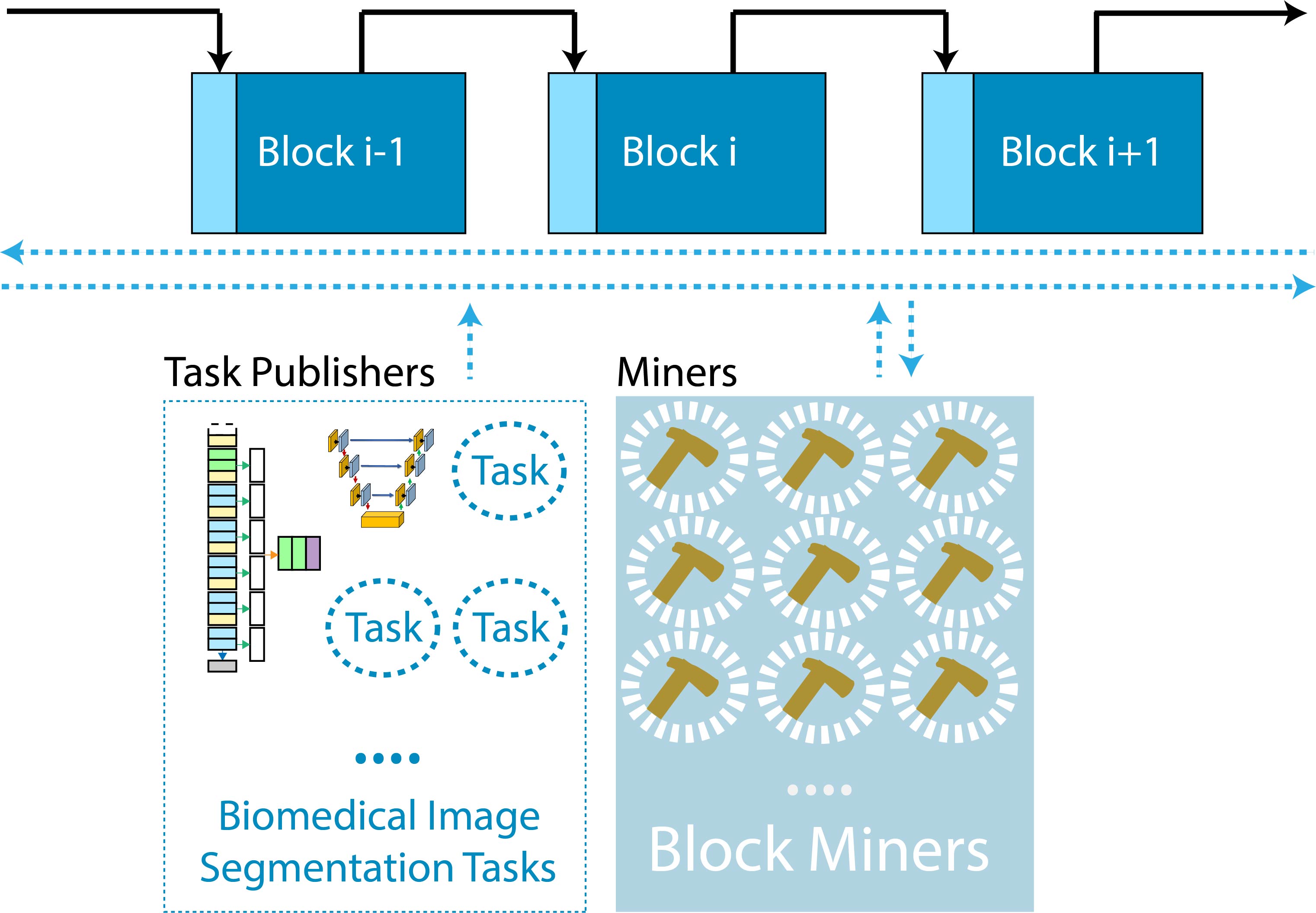
Published:
The mechanism to generate blockchain. 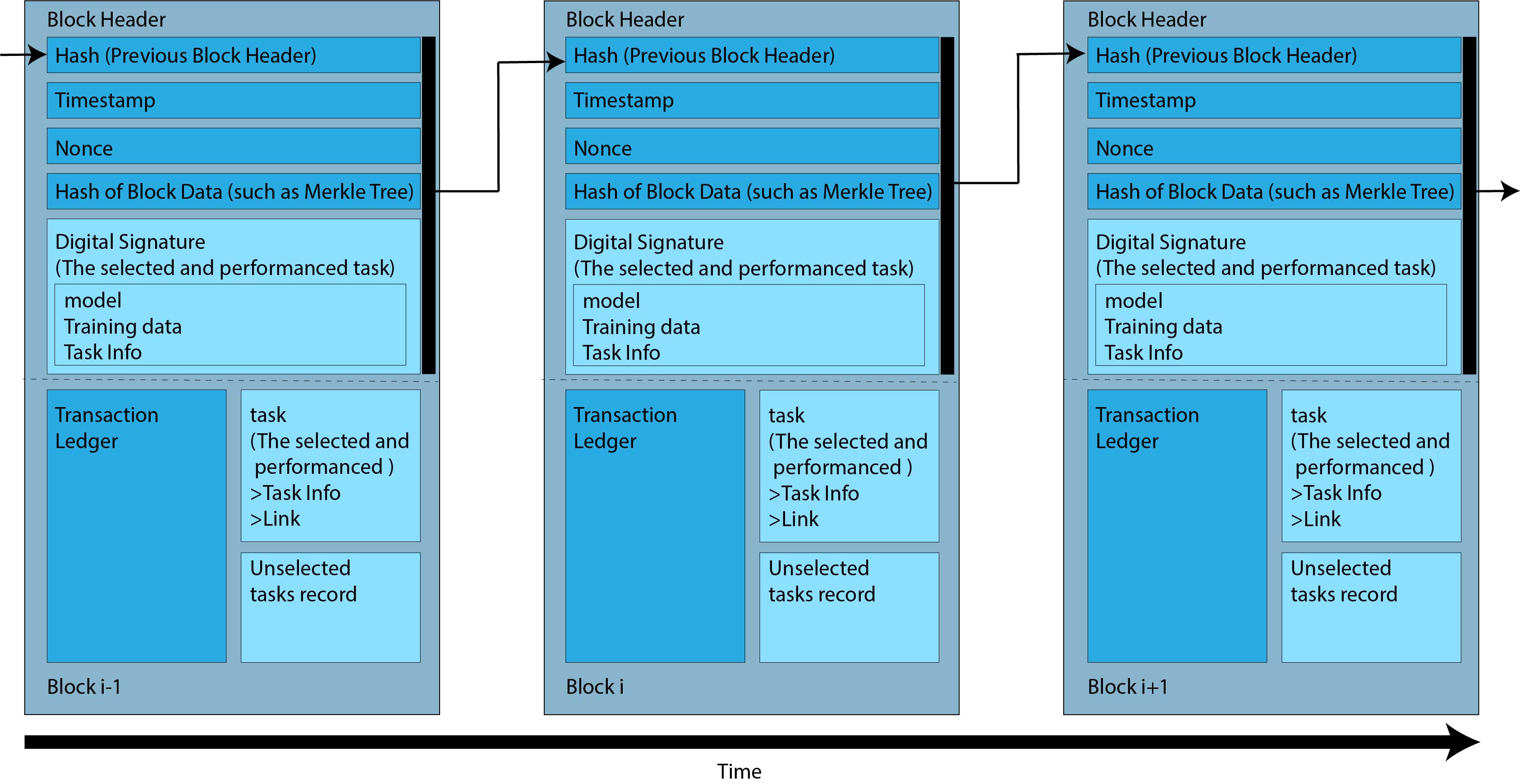
Published:
A simple demonstration of the concept. 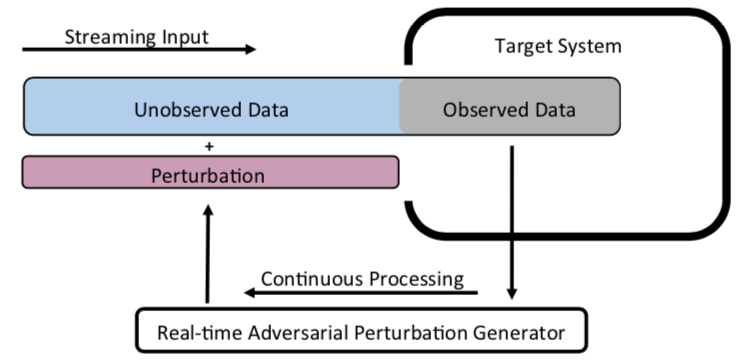
Published:
Scheduling battery and schedulable appliances. 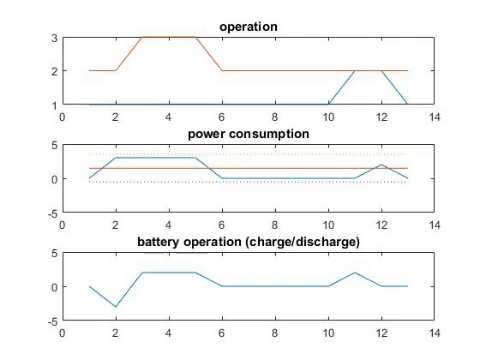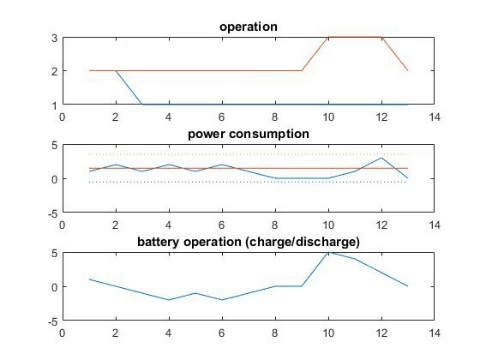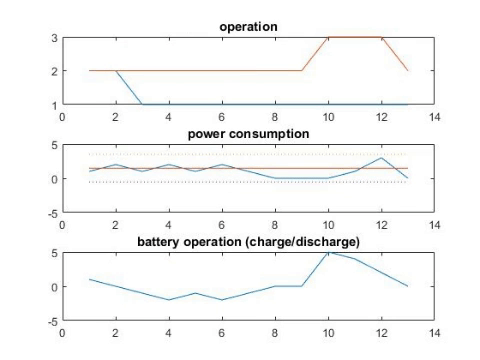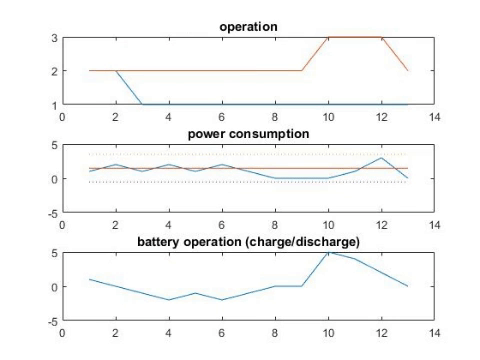
Published in 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), 2019
An enormous amount of energy is wasted in Proof-of-Work (PoW) mechanisms adopted by popular blockchain applications (e.g., PoW-based cryptocurrencies), because miners must conduct a large amount of computation. Owing to this, one serious rising concern is that the energy waste not only dilutes the value of the blockchain but also hinders its further application. In this paper, we propose a novel blockchain design that fully recycles the energy required for facilitating and maintaining it, which is re-invested to the computation of deep learning. We realize this by proposing Proof-of-Deep-Learning (PoDL) such that a valid proof for a new block can be generated if and only if a proper deep learning model is produced. We present a proof-of-concept design of PoDL that is compatible with the majority of the cryptocurrencies that are based on hash-based PoW mechanisms. Our benchmark and simulation results show that the proposed design is feasible for various popular cryptocurrencies such as Bitcoin, Bitcoin Cash, and Litecoin.
Recommended citation: Chenli, Changhao, Boyang Li, Yiyu Shi, and Taeho Jung. "Energy-recycling blockchain with proof-of-deep-learning." In 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), pp. 19-23. IEEE, 2019. https://arxiv.org/pdf/1902.03912.pdf
Published in Proceedings of the 28th International Joint Conference on Artificial Intelligence, 2019
A Smart home provides integrating and electronic information services to help residential users manage their energy usage and bill cost, but also exposes users to significant privacy risks due to fine-grained information collected by smart meters. Taking account of users’ privacy concerns, this paper focuses on cost-effective runtime scheduling designed for schedulable and non-schedulable appliances. To alleviate the influence of operation uncertainties introduced by non-schedulable appliances, we formulate the problem by minimizing the expected sum of electricity cost under the worst privacy situation. Inventing the iterative alternative algorithm, we effectively schedule the appliances and rechargeable battery in a cost-effective way while satisfying users’ privacy requirement. Experimental evaluation based on real-world data demonstrates the effectiveness of the proposed algorithm.
Recommended citation: Li, Boyang, Jie Wu, and Yiyu Shi. "Privacy-Aware Cost-Effective Scheduling Considering Non-Schedulable Appliances in Smart Home." In 2019 IEEE International Conference on Embedded Software and Systems (ICESS), pp. 1-8. IEEE, 2019. https://arxiv.org/pdf/1909.05300.pdf
Published in Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops, 2019
Biomedical image segmentation based on Deep neural network (DNN) is a promising approach that assists clinical diagnosis. This approach demands enormous computation power because these DNN models are complicated, and the size of the training data is usually very huge. As blockchain technology based on Proof-of-Work (PoW) has been widely used, an immense amount of computation power is consumed to maintain the PoW consensus. In this paper, we propose a design to exploit the computation power of blockchain miners for biomedical image segmentation, which lets miners perform image segmentation as the Proof-of-Useful-Work (PoUW) instead of calculating useless hash values. This work distinguishes itself from other PoUW by addressing various limitations of related others. As the overhead evaluation shown in Section 5 indicates, for U-net and FCN, the average overhead of digital signature is 1.25 seconds and 0.98 seconds, respectively, and the average overhead of network is 3.77 seconds and 3.01 seconds, respectively. These quantitative experiment results prove that the overhead of the digital signature and network is small and comparable to other existing PoUW designs. paper link
Recommended citation: Li, Boyang, Changhao Chenli, Xiaowei Xu, Taeho Jung, and Yiyu Shi. "Exploiting computation power of blockchain for biomedical image segmentation." In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops, pp. 0-0. 2019.
Published in Proceedings of the 28th International Joint Conference on Artificial Intelligence, 2019
In recent years, many efforts have demonstrated that modern machine learning algorithms are vulnerable to adversarial attacks, where small, but carefully crafted, perturbations on the input can make them fail. While these attack methods are very effective, they only focus on scenarios where the target model takes static input, i.e., an attacker can observe the entire original sample and then add a perturbation at any point of the sample. These attack approaches are not applicable to situations where the target model takes streaming input, i.e., an attacker is only able to observe past data points and add perturbations to the remaining (unobserved) data points of the input. In this paper, we propose a real-time adversarial attack scheme for machine learning models with streaming inputs.
Recommended citation: Gong, Yuan, Boyang Li, Christian Poellabauer, and Yiyu Shi. "Real-time adversarial attacks." In Proceedings of the 28th International Joint Conference on Artificial Intelligence, pp. 4672-4680. AAAI Press, 2019. https://www.ijcai.org/Proceedings/2019/0649.pdf
Published in IEEE Transactions on Service Computing (under review), 2020
With the increasing artificial intelligence application, deep neural network (DNN) has become an emerging task. However, to train a good deep learning model will suffer from enormous computation cost and energy consumption. Recently, blockchain has been widely used, and during its operation, a huge amount of computation resources are wasted for the Proof of Work (PoW) consensus. In this paper, we propose DLBC to exploit the computation power of miners for deep learning training as proof of useful work instead of calculating hash values. it distinguishes itself from recent proof of useful work mechanisms by addressing various limitations of them. Specifically, DLBC handles multiple tasks, larger model and training datasets, and introduces a comprehensive ranking mechanism that considers tasks difficulty(e.g., model complexity, network burden, data size, queue length). We also applied DNN-watermark [1] to improve the robustness.
Recommended citation: Boyang Li, Changhao Chenli, Xiaowei Xu, Yiyu Shi and Taeho Jung, "DLBC: A Deep Learning-Based Consensus in Blockchains for Deep Learning Services," IEEE Transactions on Service Computing (under review)
Published:
A talk is given at NSF IUCRC, University of Duke on the topic of Intelligent P-QRS-T peak detection for implantable devices.
Published:
A presentation is given at IEEE ICESS 2019 conference (Co-located with DAC 2019) on the topic of Privacy-Aware Cost-Effective Scheduling Considering Non-Schedulable Appliances in Smart Home.
Published:
An oral presentation is given at CVF/IEEE CVPR 2019 Blockchain Workshop on the topic of Exploiting Computation Power of Blockchain for Biomedical Image Segmentation (link).
Published:
A talk is given at NSF IUCRC, University of Notre Dame on the topic of ECG ST-Segment Templates Set Selection with a Recommendation System for Ultra-Low Power Implantable Devices.
CSE 20221, University of Notre Dame, Department of Computer Science and Engineering, 2017
CSE 20110, University of Notre Dame, Department of Computer Science and Engineering, 2017
CSE 20312, University of Notre Dame, Department of Computer Science and Engineering, 2018
CSE 20221, University of Notre Dame, Department of Computer Science and Engineering, 2019
CSE 40113, University of Notre Dame, Department of Computer Science and Engineering, 2019